Flowmon Anomaly Detection System - Network Detection and Response
Today, the increase in cyber-security attacks and their related risk is top of mind for many IT professionals. As such, full consideration needs to be made regarding the appropriate protections that should be in place to mitigate this risk best.
Flowmon positions its Anomaly Detection System (ADS) module at the core of these efforts, ensuring that threats can be detected and responded to as early and quickly as possible.
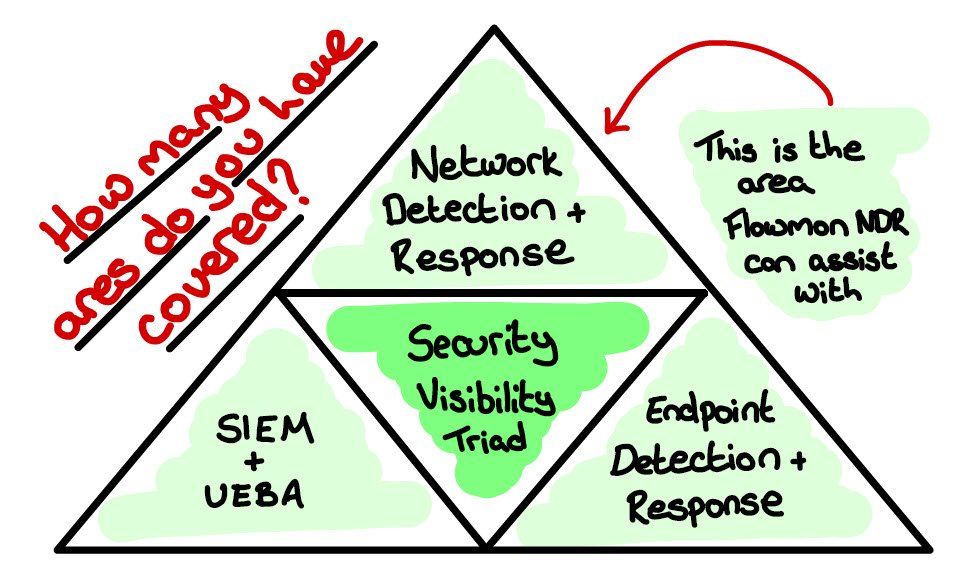
When speaking to Flowmon, they highlighted the Security Visibility Triad, a framework used by Gartner and others to help examine the three key areas that should be in place to ensure you have true security visibility. The Security Visibility Triad talks about the importance of 1. SIEM and UEBA, 2. Network Detection and Response, and 3. Endpoint Detection and Response. Flowmon focuses its efforts on the Network Detection and Response area of this triad.
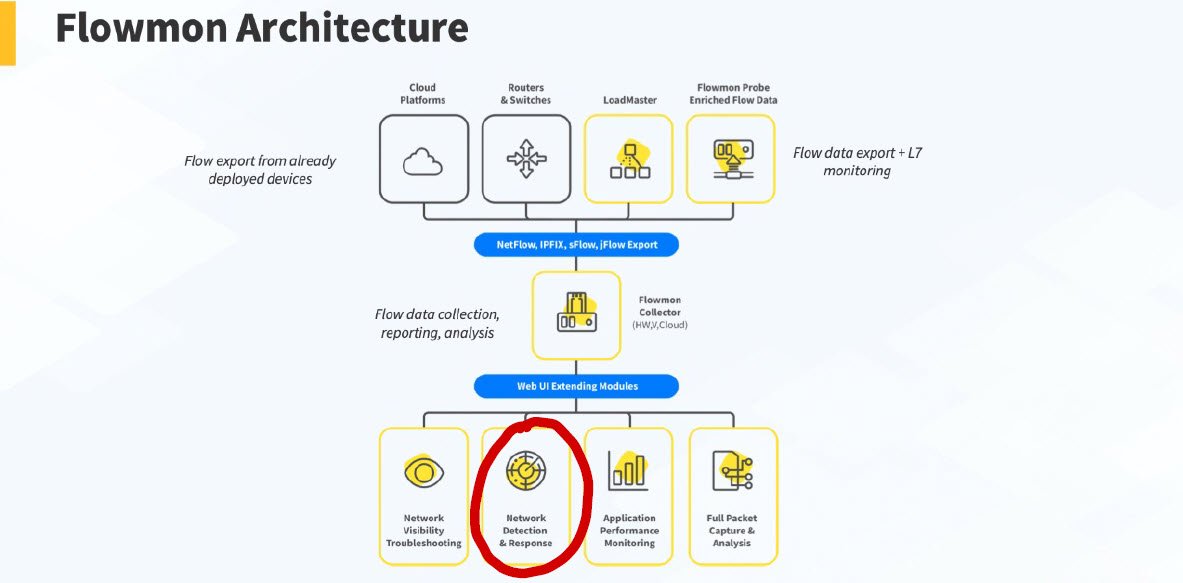
Flowmon ADS is a module for the Flowmon product set that is most commonly utilised for network visibility and troubleshooting. Because of this, the ADS module fully leverages the network architecture of Flowmon to collect its data from the network. Furthermore, it utilises network flows, enhanced with layer 7 application data provided by its probes for a unique view of what is going on within the network. You can read more about Flowmon in my previous blog.
Flowmon ADS does not rely on legacy signature-based approaches to detect the anomalies within the captured flows. Instead, it uses machine learning for wide-ranging detection, including zero-day threats.
Typical anomalies detected and alerted upon by Flowmon include:-
Attacks
Port scanning, Dictionary attacks, DoS/DDoS, Telnet
Traffic Anomalies
DNS, DHCP, ICMP, Multicast
Internal Security
Viruses, Malware, Ransomware, Botnets
Unwanted Applications
P2P Networks, Instant Messaging, Anonymisation Servies
Device Behaviour
Change of device behaviour profile
Operational Problems
Delays, Excessive load, Unresponsive services, Broken updates
Whilst how Flowmon detects the anomalies and the breadth of what it is able to detect is truly impressive, the biggest stand-out area for me was how the product allows this information to be used.
With many security products, such as NDR and SIEM solutions, they can be very good at collecting data, but in reality, they simply overload an already overworked administrator with information they can’t use. This is where Flowmon ADS is different.
Flowmon ADS not only detects the threats from the noise using machine learning but also does true route cause analysis. This allows administrators to quickly understand the type of threat, the source, the affected resources and the recommended actions.
With many sources speaking about the amount of time a threat actor may be within your network prior to detection, it is important that IT teams have the right tools to understand exactly what is happening across their network. For me, this is where Flowmon comes in, giving true visibility to Security Operations (SecOps) teams and others in IT to ensure that any threats are quickly and easily neutralised.
Below you can see my doodle covering the subject
Disclaimer: Tech Doodles through Tech Crossing Limited has been paid by Progress to create content covering the Flowmon product set. Whilst Tech Crossing Limited and the authors of this blog post have been paid to create the content, there has been no influence or editorial control by Progress.