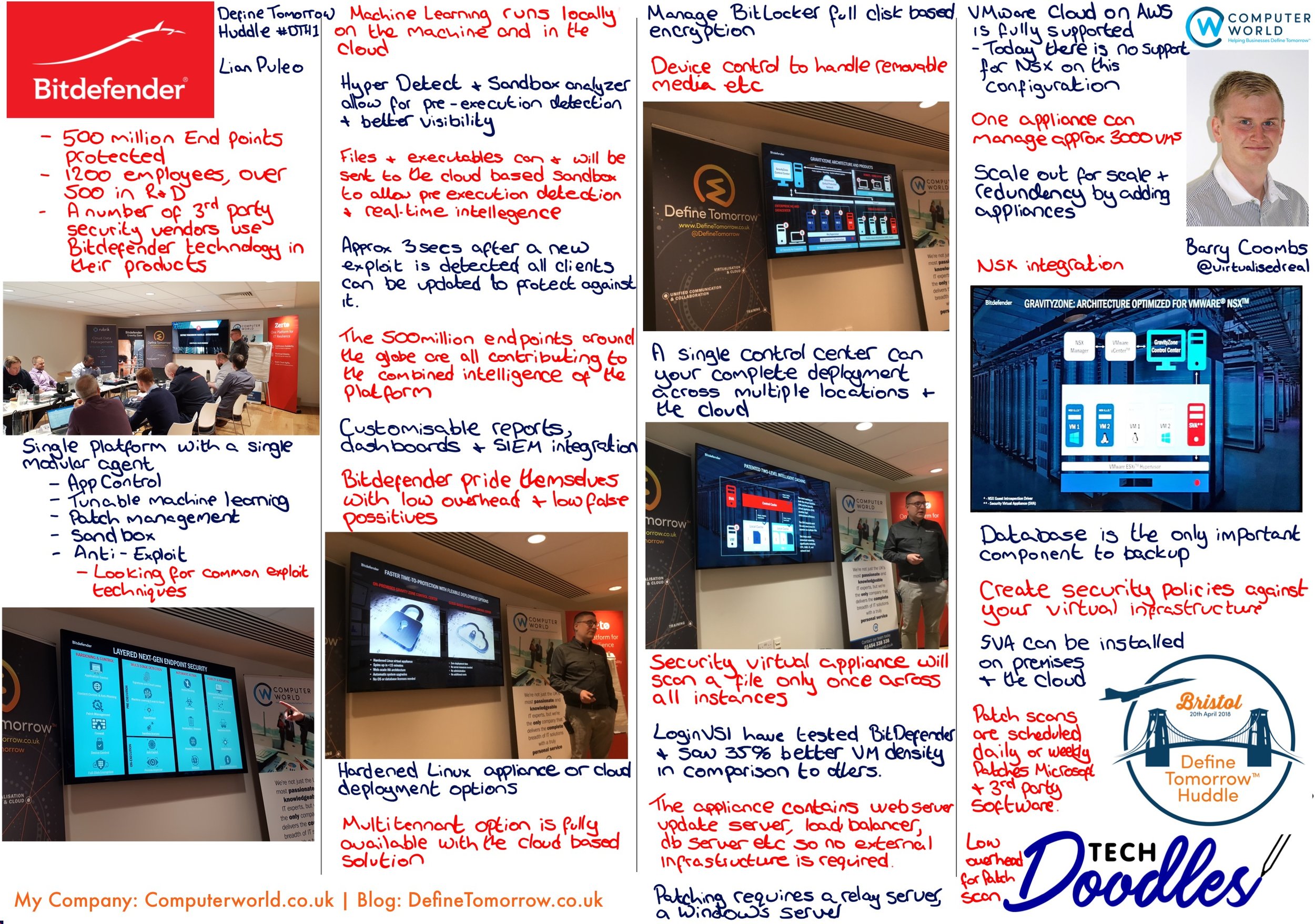
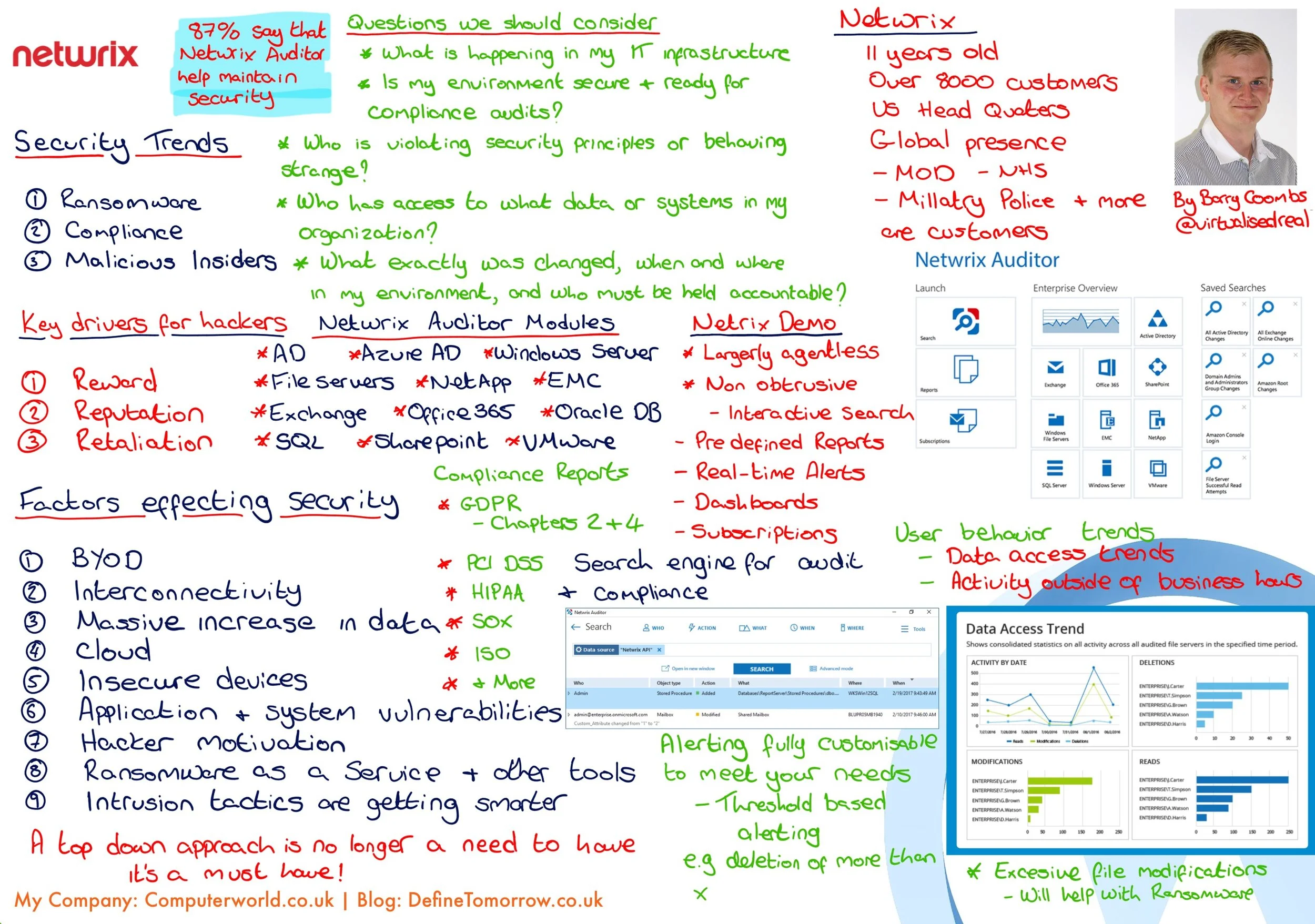
Stepping into the BAFTA HQ for the Commvault SHIFT event felt like entering a nexus where the legacy of storytelling meets the cutting edge of technology. With walls echoing cinematic greatness and rooms sponsored by the Dolby family and Steven Spielberg, the stage was perfectly set for a narrative of transformation and forward-thinking strategy in cyber resilience.
As we've observed Commvault's transition from a data protection platform to a holistic cyber resilience solution, this event painted a vivid picture of that strategic evolution.
The Hybrid IT Landscape and the Commvault Cloud
Today's IT landscape is nothing short of hybrid – offering staggering business advantages but at the same time, bringing forth data fragmentation and complex management challenges. The day was filled with conversations around the ensuing chaos and the pivotal role of a cyber resilience platform like Commvault Cloud.
NIST Framework in Focus
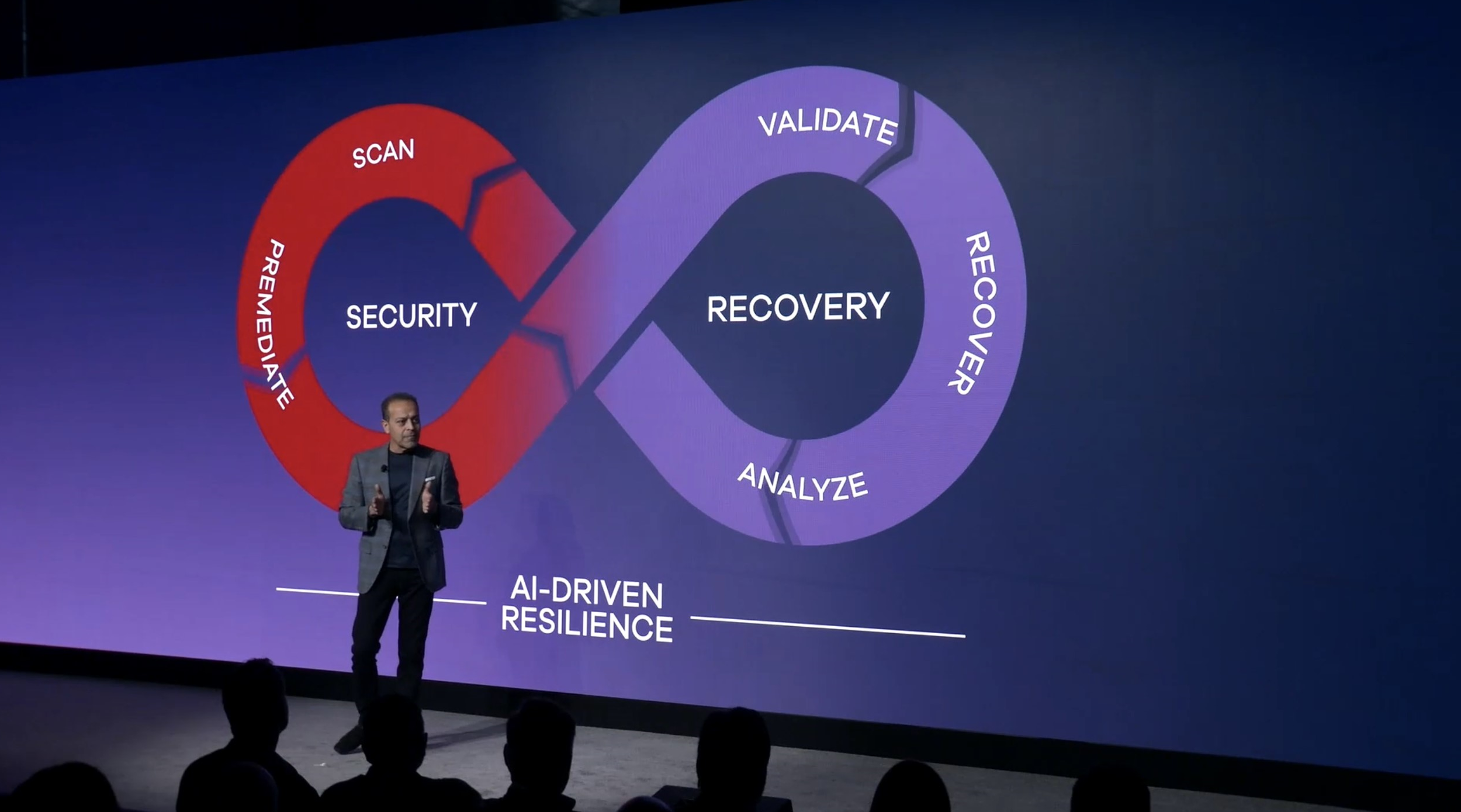
A significant part of the presentation revolved around the NIST framework, which is fundamentally a blueprint for improving cybersecurity and resilience. The framework lays out five key functions – Identify, Protect, Detect, Respond, and Recover – that help organisations develop a robust cybersecurity posture. The message was clear: whilst Indentify, Detect and Protect often takes the limelight, respond and recovery is just as crucial. The focus on thorough testing and robust recovery plans is not just recommended; it's essential.
Innovative Recovery with Cleanroom Technology
A standout feature that piqued interest was Commvault's cleanroom recovery functionality. In the event of a breach, the ability to swiftly and safely recover is paramount, and Commvault's solution facilitates this by enabling businesses to recover quickly into Azure. This isn't just about speed; it's about providing a controlled environment for both testing and actual recovery scenarios, automating the setup of the landing zone in the process.
Meet Arlie: The AI Virtual Assistant
Another highlight for me was the introduction of Arlie, Commvault’s AI virtual assistant. Arlie takes user interaction to a new level, providing insights and support embedded right into the AI. It's not just about delegating tasks; it's about empowering admins with the knowledge to carry out these tasks themselves – a truly educational approach that resonates with our belief in not just delivering solutions but also delivering knowledge.
Conversations with the Commvault Team
The day culminated with an influencer and analyst session, offering us a golden opportunity to engage with Commvault's key team members. It was more than just a chance to see the technology – it was a window into the minds shaping the technology, understanding the 'whys' and 'hows', and witnessing the solutions in action.
Wrapping Up an Enlightening Day
As the event wrapped up, it was clear that Commvault is not just participating in the cyber resilience conversation; they're actively sculpting it. With the community buzzing, the Cleanroom Technology on the horizon, and the prospect of getting hands-on with Arlie, it’s safe to say we're not just excited – we're looking at the future of cyber resilience with eyes wide open.